This post was most recently updated on August 31st, 2023.
5 min read.This article explains another small but significant gotcha you “just need to know” when working with certificates and certification authorities, and you – just like me – are for some reason still using Windows as your workhorse. I’ll go through how to export the private key that has been stored on your machine when you generated a Certificate Signing Request (or a “Certificate Enrollment Request” if you’re speaking Contosoan”) to get someone to issue you a certificate according to your specification.
I’ll also go through the confusing terminology and some other points about the process. It’s a part of my ongoing learning journey, too :)
Background
Lately, I’ve been working a lot with AKS. And while working with AKS, you run into all kinds of requirements for certificates. And when working with certificates, you’ll probably end up requesting new ones occasionally (instead of just self-signing everything) – and to upload your fancy certificates to a form AKS understands (“TLS” secrets), you’ll need a certificate and a matching private key.
Makes sense. But where do these 2 come from?
Solution
Well, the short answer is that the certificate you get from a Certificate Authority (or, as it quite often actually happens, your IT team), but they usually only generate a certificate for you based on a CSR – a Certificate Signing Request – which is something you create.
And creating the CSR stores the private key on your machine. And almost stashes it away, if you’re using Windows. This guide explains how to find it!
Time needed: 10 minutes
How to export a private key generated for a CSR using Certificate Store on Windows?
- Open the Windows Certificate Store (certlm) for Local Computer (not Personal!)
Opening the Certificate Store is going to be your first step. You’ll probably want to open it for Local Computer – not your personal one – as at least some tools to generate CSRs place the private key there.
Do all tools do that, though? I don’t know. I haven’t tried them all yet!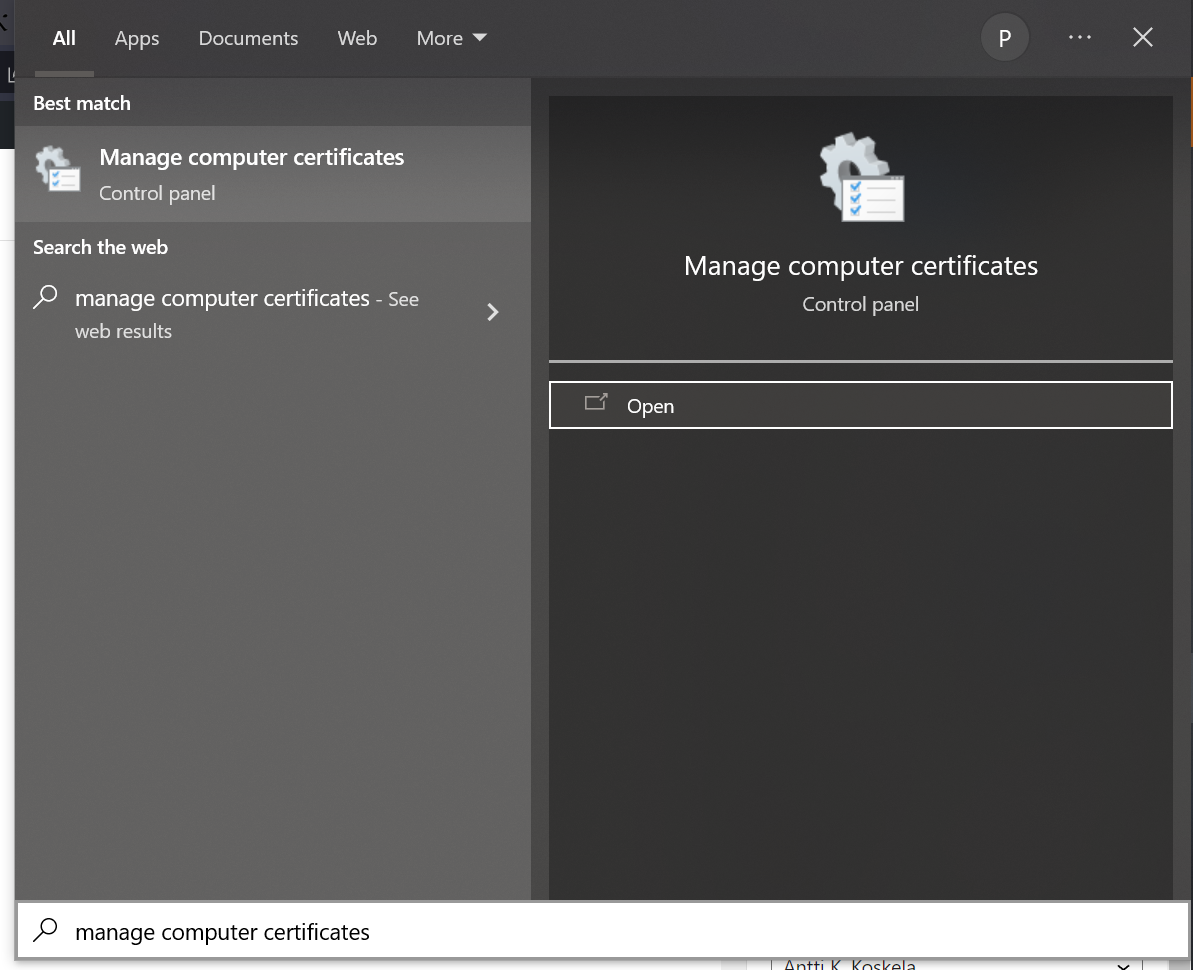
- Navigate to Certificate Enrollment Request > Certificates
From the left hand side “folder” navigation, select “Certificate Enrollment Requests”, and then “Certificates” – and you should be presented with a list of dummy certificates. They represent certificates you’ve requested from an authority or issuer – they aren’t actual certificates! But they do contain the private key…
- Select the domain you created the CSR for
You should probably know the host name or domain you generated the Certificate Signing Request for – find it in the list.
- Export the private key
Now we’ll use the extremely user-friendly and straightforward UI to export the private key! 😉
Jokes aside, a couple of steps to go through, really: Right-click and select “All Tasks > Export” > “Next” > “Yes, export the private key” > and whatever you need to do to get the private key out of there. If you have to enter a password (and you probably will), be sure to remember it :) Encrypting the .pfx and the key itself are the only things this is used for.
Note: Please only use boring characters. This password can not contain any extra-safe (or as we call them in Europe, normal and in-every-day-use) characters such as Ö, Ä or Å.
Just call it “password” or something. Maybe add a number in the end for good measure.
Name the file to mykey.pfx and place it in C:\temp\export (or whatever else location you like). - Install OpenSSL
Now we’ll use a tool called OpenSSL to export the key from the .pfx file. Figuring out where to get that tool can be a pain, but this wiki maintains a nice list of mirrors and tool versions for you.
Or you can just use winget:winget install -e --id ShiningLight.OpenSSL - Use OpenSSL to export the key to console from the .pfx -file
Anyway – here’s what to run in command prompt, PowerShell, or a shell of your choice:
cd C:\temp\export
openssl pkcs12 -info -in mykey.pfx -nodes
That should bring up a nice, long output of certificate details. You’ll want the RSA PRIVATE KEY, and you’ll find it nicely in caps. Copy it from the output. Save it to my.key or similar file. - Use OpenSSL to export the key to a file from the .pfx file
Now we’ll export the key to a file. In the sample below, I’ll presume your .pfx password was, well, “password”, and that you’ll just reuse it for the exported, encrypted key:
openssl pkcs12 -in mykey.pfx -nocerts -out mykey-encrypted.key
Enter Import Password: password
Enter PEM pass phrase: password
Verifying - Enter PEM pass phrase: password
Now we’ll have an encrypted key (key-encrypted.key). That might not be very useful to us, and if we want to export it to be unencrypted (someone might even call it “decrypting” the key!), we’ll need to do this:openssl rsa -in mykey-encrypted.key -out mykey.key
Enter pass phrase for .\key-encrypted.key: password
writing RSA key
And now we’ll have mykey.key that is unencrypted.
That’s it! You should now have the private key. Now you can proceed to compare it to a certificate to make sure they match, or do something else with it.
Questions, answers, and interesting discussion points
Ah, well this is a source of some confusion! When you generate a CSR in Windows Certificate Manager (a Snap-in “extension” of Microsoft Management Console – mmc.exe), it’s actually stored under a folder called “Certificate Enrollment Requests”.
If you want to add to the confusion, it’s a great idea to call the dummy certificates in this folder “CERs” (abbreviation from Certificate Enrollment Request). Please don’t do that though, since a .cer -file is something else.
The dummies in that folder are actually CSRs that appear to be certificates. You can export them as .pfx – further adding to the confusion!
But the main point of the story is that a “CSR” and a “Certificate Enrollment Request” are the same thing, just in a really different format.
That’s going to be very subjective – but I’ve found DigiCert’s certutil.exe really useful!
You can use it to generate a CSR, that will – very conveniently – end up in your Computer’s Certificate Store’s Certificate Enrollment Requests. That way you will (initially) get the “standard”, PEM-formatted CSR, and the private key (and other CSR details) will get stored in your Certificate Enrollment Requests as something you can export in .pfx.
Confusing, but kinda convenient.
However, you can also create CSRs with OpenSSL or even in some random online tool, if that’s to your liking.
References
- On CSR vs Certificate Enrollment Requests differences:
- CSOM suddenly throwing exceptions when trying to access list contents in SharePoint? A weird fix. - April 2, 2024
- “Predefined type ‘System.Object’ is not defined or imported” and other System namespace stuff missing in your solution? - March 26, 2024
- How to import GraphQL schema to Postman in Windows? - March 19, 2024