This post was most recently updated on August 31st, 2023.
4 min read.This post explains how to verify a private key (possibly a .key file) that you somehow got your hands on, that matches a certificate file (.cer) you also somehow are in possession of. I have no idea where I got mine, but I had to figure out how to make sure a key and a certificate matched before I uploaded mine to AKS (Azure Kubernetes Service).
Problem
This is yet another article where I document how to work around an issue, so I can do it when I run into the same issue the next time :)
Note, that I’m not a certificate expert. Far from it! Take my advice with a grain of salt.
Anyway – I had to do some AKS (Azure Kubernetes Service) configurations that required a new domain and a new associated SSL certificate to go with it. This required running something along the lines of:
kubectl create secret tls my-tls-secret --cert=path/to/cert/file --key=path/to/key/file
But before getting there, I needed to upload matching key and certificate files. And as luck would have it I had PLENTY of keys and certificates lying around at that point. But once I found a key and a certificate I liked, how could I make sure they matched one another?
Solution
OpenSSL to the rescue! With OpenSSL, you can (with some interesting steps) verify whether a cleartext key and BASE64-encoded certificate match.
The following step-by-step how-to will guide you on verifying your .key file and .cer/.crt/.pem/.der files match.
Time needed: 10 minutes
How to verify if a .key file matches a certificate file?
- Prerequisite: install OpenSSL
OpenSSL is a command-line tool you can use to do all kinds of black magic to certificates. But today, we’ll use it to verify your private key matches your certificate.
The first thing to do is to download the tool. They don’t want to make it too easy, but you should be able to find the latest version here. - Have .cer and .key in the same folder
Move all of your certificate files to one folder, open Terminal, and change to that directory.
You’ll need a .cer file (in my example, my.cer) and a .key file (my.key, unsurprisingly). The latter should look somewhat like this:
—–BEGIN RSA PRIVATE KEY—–
ALOTOFCHARACTERSHEREFORQUITEAFE
WLINESITSQUITEDIFFICULTTOREADYFRA
NKLYBUTYOUDONTNEEDTOCAREABOUT
THAT
—–END RSA PRIVATE KEY—– - Transform your certificate to PEM format
If your .cer file is not BASE64-encoded when you open it up in VS Code or a similar text editor, you need to transform it.
The easy rule is the certificate needs to be in Latin characters and start with this:
—–BEGIN CERTIFICATE—–
and end with:
—–END CERTIFICATE—–
If it’s not, it’s probably a certificate with DER encoding. You can’t actually decipher this from the file format (or extension) because it has almost no relation to the actual contents of the file. Doesn’t seem like standards in the world of certificates are very strict.
Anyway – your certificate, for this tutorial, needs to be not DER encoded. And one way to decode it is this:OpenSSL x509 -inform DER -in my.crt -out my.cer
If it already was BASE64-encoded, you can use the certificate as it is. The rest of the tutorial assumes it’s called my.cer, but it could be .crt or .pem, too, and still be according to the standard.
Clear as mud! But you should now either have a usable .cer file, or an error about being unable to read the contents. In both cases, you can proceed. - Calculate the modulus from your certificate
Now we’ll calculate the modulus for your certificate. You don’t need to understand this. I don’t either (not really anyway). But it’ll help us.
If you now have a .cer file (the last step was successful), this should work:openssl x509 -noout -modulus -in my.cer
If the last step failed, make sure the file only has the stuff between —–BEGIN CERTIFICATE—– and —–END CERTIFICATE—– (and before you comment, I KNOW it can have extra stuff because who cares about standards, but for whatever reason removing extra stuff helps), no extra whitespace, is actually readable, and then retry running it again.
If this fails, too, your certificate was probably rubbish. Get a new one.
If it produced an interesting output and not an error, take note of the output. You’ll need it for comparison. - Calculate the modulus for your private key
Now, for your private key file (my.key in my sample), run this:
openssl rsa -noout -modulus -in my.key
This is the second output you need to compare. - Compare the 2 values
If the modulus output you get from the 2 commands matches, the private key and your certificate are a pair.
That looks somewhat like the below: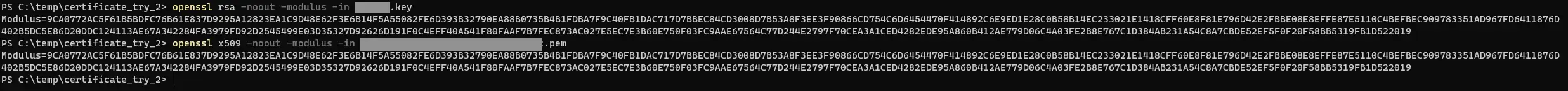
And that was that! With any luck, you should be done :)
Still unclear? Running into new issues? Let me know in the comments -section below and I’ll see what I can do to help!
References
- DigiCert describes the Modulus check (although they don’t describe the first few steps):
- Confused by DER, PER, CER, and of course CRT, CSR, KEY, PFX, RSA, X509, and everything else? This one is a pretty good explainer:
- How to generate Certificate-Signing Requests using OpenSSL - June 18, 2024
- Home Assistant 2024.4 changes weather forecasts – what to do? - June 11, 2024
- External path “**” cannot have more than one “*” wildcard with vite? - June 4, 2024




