This post was most recently updated on February 27th, 2022.
3 min read.Another day, another unsuccessful authentication attempt, and another cool error code. I encountered his one whilst building a little POC that was supposed to authenticate against Graph API. This time, I was thrown an “AADSTS700054” error…
But no worries! This article will explain to you how to fix it, at least in a couple of different cases! :)
Problem
When developing your client-side solution (an SPFx web part, React app, ASP.NET MVC application with some client-side components… Your pick!), you run into this error when your code tries to authenticate against Azure AD:
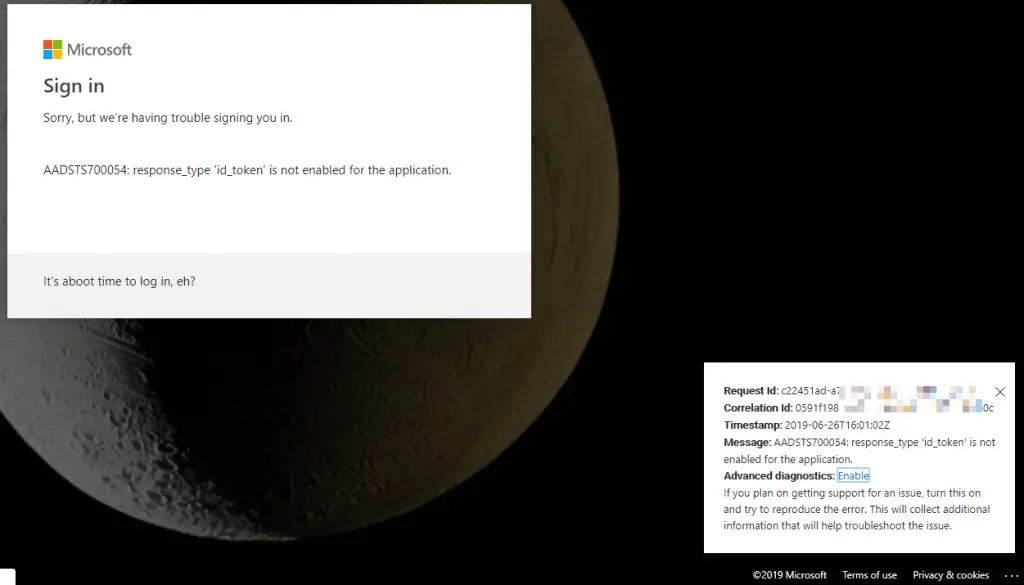
AADSTS700054: response_type 'id_token' is not enabled for the application.
And nothing else, really. That’s all.
Not super descriptive, is it? Below, you can find a screenshot of such an issue:
What do?
Reason
Your app’s authentication provider is currently not allowed to return a token that’s required for the OAuth2 implicit flow. This flow is a simplified authentication flow, where your successful authentication request will directly result in an access token to be returned to your app.
Since your app is requesting the token, but the authentication provider can’t return it, an error is thrown. If you’re the developer (or an administrator) of the app, you can fix this – if not, you’ll need to find out who is and report the issue to them… 😅
Anyway – there are a couple of different switches, that might be stopping the token from being returned. Let’s take a look, then!
Solution
There are 2 steps that you need to take to fix this issue. Luckily, as long as you have access to the app registrations, both steps are simple.
First of all, consider whether you need the implicit flow or not, based on what I wrote earlier. Maybe you don’t – and you should be using something else instead.
If you do, proceed with the steps below.
Time needed: 10 minutes
Fixing “AADSTS700054: response_type ‘id_token’ is not enabled for the application” error
- Enable the implicit authentication flow
You’ll need to make a simple app manifest change to enable the authentication with the implicit flow in the first place.
See the article below for instructions on how to enable the implicit authentication flow for your app:
Fixing issue “AADSTS70005” by enabling the implicit authentication flow for your Azure AD app
When that’s done, and if you still have issues, see below as well: - Enable returning the tokens
Okay – next we need to make sure our registered app is allowed to return those tokens when requested. The configuration page on AAD says the following about the implicit flow (implicit grant):
Allows an application to request a token directly from the authorization endpoint. Recommended only if the application has a single page architecture (SPA), has no backend components, or invokes a Web API via JavaScript.
To enable the implicit grant flow, select the tokens you would like to be issued by the authorization endpoint…
Okay, so that means we’ll just need to navigate to the following path:
Azure Portal > Azure Active Directory > App Registrations > Authentication > Advanced Settings > Implicit grant
Enable “ID tokens” as shown below.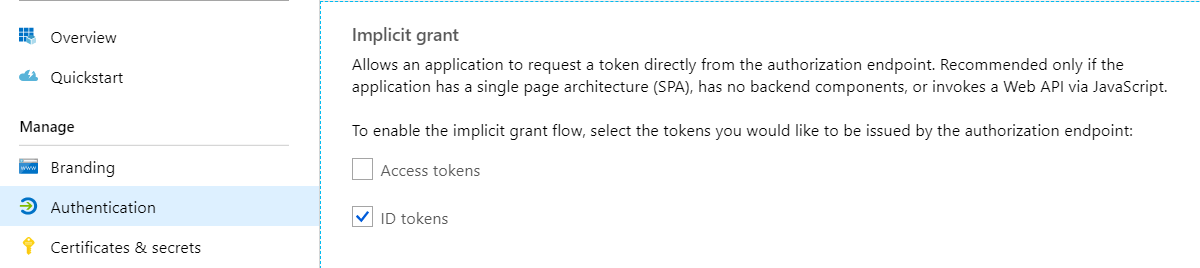
- Save and retry
Click Save, head back to your app – it should work now!
All good now? Let me know in the comments section below!
- “Critical Error – Your Start menu isn’t working” - April 23, 2024
- How to export a CSR you’ve created on Windows? - April 16, 2024
- How to output all Environment Variables in Azure DevOps with PowerShell? - April 9, 2024