Home » GraphAPI
This article explains how to easily add additional headers to the Graph API calls you make in PowerShell using Invoke-PnPGraphMethod commandlet. There’s a convenient sample for you to copy-paste and some basic explanations on what we’re doing below. Background Every now and then, I need to make some Graph API…Continue reading How to add AdditionalHeaders to Invoke-PnPGraphMethod?
This article explains one possible fix to an annoyingly generic exception thrown by the Microsoft Graph API (namely, “Unsupported or invalid query filter clause specified for property”) or an even more generic exception thrown by PnP PowerShell (“Exception of type ‘PnP.PowerShell.Commands.Model.Graph.GraphException’ was thrown.”) when you’re trying to query Graph API…Continue reading One way to fix “Unsupported or invalid query filter clause specified for property” for your Microsoft Graph API queries
This article explains a quick fix to a small but annoying issue: Microsoft Graph API SDK persistently returning null values for most properties of your Microsoft.Graph.User objects. The issue might happen when using either the Graph API SDK or just calling the REST API directly. Both options are entirely acceptable,…Continue reading How to fix Graph API returning null properties for Users?
Man, do I run into all kinds of issues with the smallest Azure Functions that I develop. And it’s mostly my fault. The silver lining is that you’re here to read this article, so you probably ran into this same stuff. Well – you should be happy to hear that…Continue reading Errors loading an assembly that’s using Microsoft Graph API
Hey, another funny case. “Funny” as in “the error message is misleading and googling didn’t really help”, but also as in “a colleague knew the answer right off the bat because he already fixed it in another project”. This time the documentation was in fact there, it just wasn’t there…Continue reading Graph API throws “$count is not currently supported.” when you KNOW it’s supported?
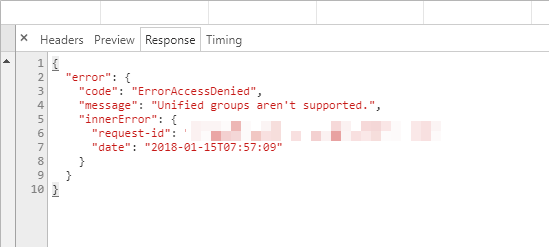
When trying to use some functionality, that relies on Unified Groups, you’re getting errors in the console, similar to this: “Unified Groups aren’t supported.” In truth, this most likely means, that Unified Groups (that’s the internal/technical name for Office 365 Groups) is not enabled for this particular user. That breaks a bunch of…Continue reading How to solve the “Unified Groups aren’t supported.” -error
Office 365 Planner is a neat tool for task management. However, when you, for whatever use case, need to form URLs that point you towards a single task (or a bucket, or a plan for that matter), you might run into trouble with how the URL is formed. Custom domains…Continue reading How to form links to Planner tasks
Okay – yet another weird issue, and a hacky workaround. I was developing an app that was calling a SharePoint site through Graph API, using jQuery $.ajax call (developed in TypeScript), and ran into surprising 401 errors. I did find a workaround but am also working on an actual fix.…Continue reading Call to sites Graph API requires “owner” permissions for site collection regardless of app permissions
Have you run into an AADSTS65001 error with your application, that tries to authenticate against Azure AD? I sure have – seems to happen at least every other time when I’m building something that uses AAD to authenticate against SharePoint. Fixing issues with Azure AD authentication for Enterprise applications can…Continue reading 4 ways to fix error AADSTS65001 (The user or administrator has not consented to use the application)