This post was most recently updated on February 26th, 2023.
3 min read.This was a peculiar case! An issue I hadn’t run into before, and luckily a disturbingly simple fix. But first, let’s set up the scene: We were running a long-ish PowerShell script using a Global Administrator account. One part of the script was supposed to add and deploy a couple of SharePoint apps. But while running Add-PnPApp, we ran into errors:
Add-PnPApp -Path $path -Scope $app.Scope -ErrorAc… , Error: {"error":{"code":"-2147024891, System.UnauthorizedAccessException","message":{"lang":"en-US","value":"Access denied. You do not have permission to perform this action or access this resource."}}}Oh. That’s… A bit surprising for a Global Administrator, right? What’s causing this?
Security. It’s always security…
This particular customer was fairly strict about their security. This had caused them to remove a lot of the built-in security principals from a lot of places – along with any created SharePoint sites included. This is not necessarily a bad thing, but security hardening might break things if you don’t know what you’re doing.
In this particular case, the security hardening was also applied to the app catalog site of the SharePoint tenant. This means that their built-in principals like “SharePoint Service Administrator” and “Company Administrator” were removed. Actually, everyone but their one service account (which wasn’t the Global Administrator account we were using here), was removed.
Consequently, SharePoint and Global Administrators lost admin permissions on the site, although they still retained access there (it’s kind of difficult to completely block a Global Administrator from a site, after all).
Probably needless to say, this configuration blocks even Global Administrators from adding or installing new apps using the PnP commandlets – like Add-PnPApp – or even using the GUI.
Solution: Don’t mess with the built-in principals!
A lot of authentication issues in SharePoint are caused by someone messing with the built-in credentials.
In case you run into this issue, make it the first thing you do to verify, that the following built-in principals are in place. So if you already have messed with them, add them back!
The following principals are required for the App Catalog site to make Add-PnPApp to work:
- Company Administrator
- Maps to Global Administrators
- SharePoint Service Administrators
- Maps to, well, SharePoint Service Administrators
Whichever account you’re using to run Add-PnPApp needs to be an admin/owner on the App Catalog site.
How to fix this and get your Add-PnPApp to work?
Browse to your SharePoint Administration, select Site Collections (or Sites) and find your App Catalog from the list. Select it, and select “Owners > Manage Administrators”. The screenshot below shows what the configuration should look like.
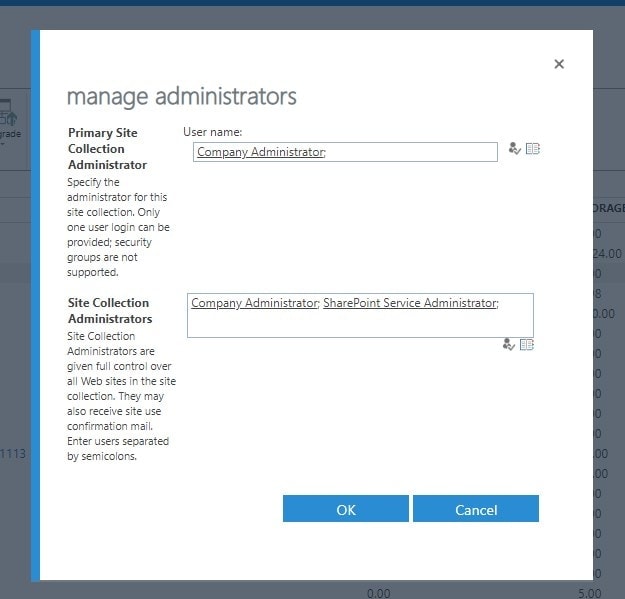
Since this event, I’ve paid more attention to App Catalog permissions, and I’ve seen them deviate from the configuration above on some other tenants, too. Perhaps there’s something interesting also happening in the initial provisioning of the App Catalog, and at least sometimes the built-in principals are shut out of the created site by accident. This functionality doesn’t seem like it would make much sense – but maybe it’s an unintended implementation by Microsoft.
Be that as it may, adding the built-in service principals Company Administrator and SharePoint Service Administrator to the administrators of the app catalog site should fix the commandlets for you.
If adding the principals doesn’t help…
If adding the Company Administrator and SharePoint Service Administrator principals don’t help you, then you might be dealing with a bit of a more complicated issue. Unfortunately, it’s fairly typical for the App Catalog site collection to become corrupted.
If you don’t have any apps deployed yet, it’s most of the time safe to just remove the site collection and recreate it – but if you can’t do that and this error keeps happening, your best bet might be to contact Microsoft Support.
- Am I the problem? Even onboarding to the Apple ecosystem failed miserably. - July 8, 2025
- Any kubectl command throws “Unhandled Error” err=”couldn’t get current server API group list: Get \”http://localhost:8080/api?timeout=32s\”: dial tcp [::1]:8080: connect: connection refused” – what do? - July 1, 2025
- “Sync error. We are having trouble syncing. Click ‘Sign in again’ to fix the issue.” in OneNote? Let’s fix it! - June 24, 2025