This post was most recently updated on December 7th, 2022.
3 min read.Have you run into the cryptical “AADSTS50059: No tenant-identifying information found in either the request or implied by any provided credentials.” error? I have. This post will tell you how to fix it.
How to fix AADSTS50059?
I encountered this error while trying to reload a page with some JavaScript that authenticates against Graph API. It completely blocks the functionality, as it redirects the user to the login page, but instead of successfully logging in (and perhaps redirecting back), it fails with an error.
Luckily, at least in my case, this was easily fixed! Your error might look something like this:
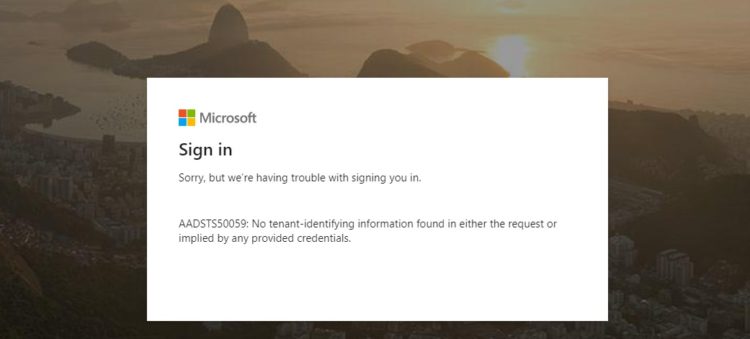
Sorry, but we’re having trouble with signing you in. AADSTS50059: No tenant-identifying information found in either the request or implied by any provided credentials. Request Id: <guid> Correlation Id: <guid> Timestamp: 2019-11-27T20:58:36Z Message: AADSTS50059: No tenant-identifying information found in either the request or implied by any provided credentials.
Okay – so the error claims Azure AD fails to recognize your tenant, as the request or provided credentials didn’t provide that.
… But is that even true?
The URL of the login page will look something like this:
https://login.microsoftonline.com/common/oauth2/authorize?response_type=token&client_id=[guid]&resource=https%3A%2F%2Fgraph.microsoft.com&redirect_uri=https%3A%2F%2Fdomain.sharepoint.com%2Fsites%2F[site]&state=[guid]%7Chttps%3A%2F%2Fgraph.microsoft.com&client-request-id=[guid]&x-client-SKU=Js&x-client-Ver=1.0.14&prompt=none&login_hint=user.name%40domain.com&domain_hint=domain.com&iframe-request-id=bc2a9682-570c-40d4-83a8-5b9c402e1300
So.. Wait a minute. The login URL actually has all the info about the tenant and everything! You should be able to log in with that. What’s wrong, then?
The issue is, that you’ve already got login information on your machine – just not the correct one for this tenant! It’s all cached in the Local Storage, and the info conflicts with what you have in the URL. So the whole login process is trying to implicitly use the wrong cached credentials to log in to the tenant automatically.
Solutions
After originally writing this article in 2018, I actually uncovered another way to mess up your authentication flow in your code that results in getting the AADSTS50059 error.
However, let’s go through the easy, user-oriented fix first, and then briefly take a look at the more developer-centric option!
Solution 1: Remove everything related to ADAL from Local Storage
ADAL login, when successful, caches the login info into your browser’s local storage. That’s convenient, as it eliminates the need to log in again anytime soon, but in a situation where you’ll be authenticating against multiple Azure AD instances (such as when you’re switching between different SharePoint tenants running code against Graph API), it’ll mess up the authentication. You’ll be trying to use the wrong tenant’s info automatically – and there’s very little you can do about it by default!
The solution is simple – you’ll just need to clear the browser’s local storage. Below, I’m showing what to remove in case you’re using Google Chrome. You’ll need to hit F12 to open developer tools, browse to the “Application” tab, and then find your tenant from the “Local Storage” -section.
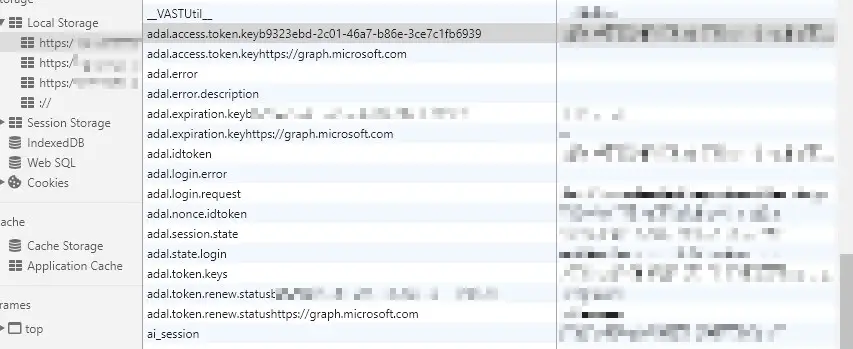
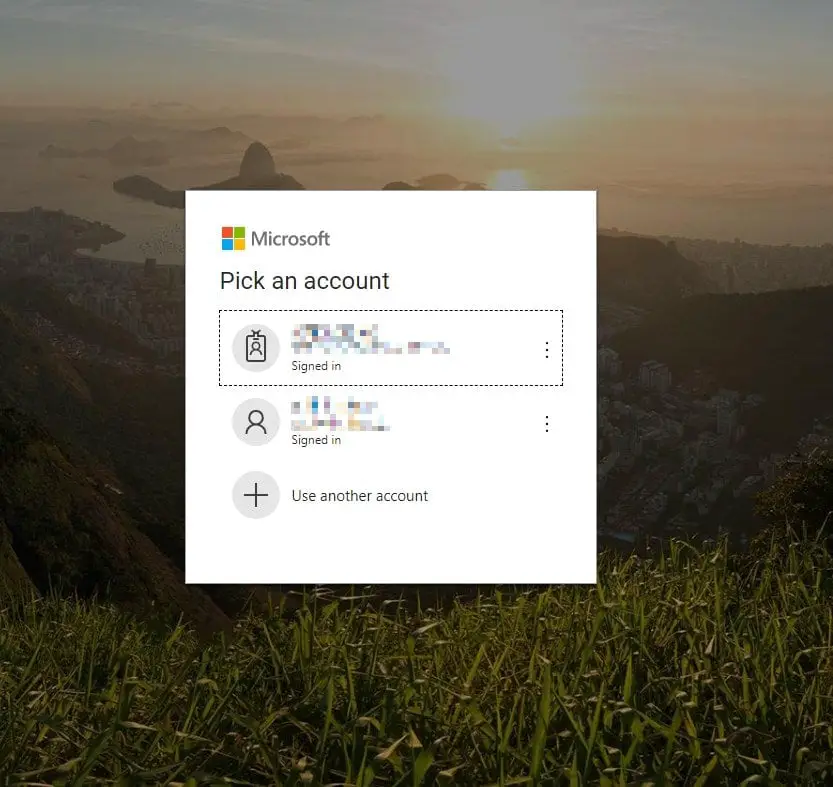
After removing all the storage entries for ADAL, refresh the page that threw the error before, and you should be greeted with a fresh, neat login screen!
At this point, whatever you’re selecting, will then be cached for your browser, and used automatically the next time you try to log in again.
Solution 2: You’re not crafting the authentication request properly. Fix it.
Okay, so let’s take another look at the authentication URL, shall we?
https://login.microsoftonline.com/common/oauth2/authorize?response_type=token&client_id=&resource=https%3A%2F%2Fgraph.microsoft.com&redirect_uri=https%3A%2F%2F.sharepoint.com%2Fsites%2F&state=%7Chttps%3A%2F%2Fgraph.microsoft.com&client-request-id=&x-client-SKU=Js&x-client-Ver=1.0.14&prompt=none&login_hint=user.name%40domain.com&domain_hint=domain.com&iframe-request-id=bc2a9682-570c-1337-83a8-5b9c402e1300
So, quite a while after the original issue I documented, I encountered another way to mess up. Apparently, a careless developer might be crafting the query based on the email address of the user. However – that is not necessarily what you need to use!
The email in question needs to be the UPN of the user, not an email address. So wherever you’re picking your user’s account name from, make sure to not use “just” an email address – fetch the UPN instead.
So, that’s the 2 things to check. For now, you should be good!
- CSOM suddenly throwing exceptions when trying to access list contents in SharePoint? A weird fix. - April 2, 2024
- “Predefined type ‘System.Object’ is not defined or imported” and other System namespace stuff missing in your solution? - March 26, 2024
- How to import GraphQL schema to Postman in Windows? - March 19, 2024